AWS PrivateLink
This page describes the setup process for PrivateLink, an Amazon service that securely connects a Virtual Private Cloud (VPC) to AWS APIs without creating an external IP address. You need an AWS account with PrivateLink enabled to use this feature.
AWS General Workflow
-
Begin creating a paid-tier TigerGraph cluster in a region that supports private access.
-
Select “Private“ for the TigerGraph Endpoint Type.
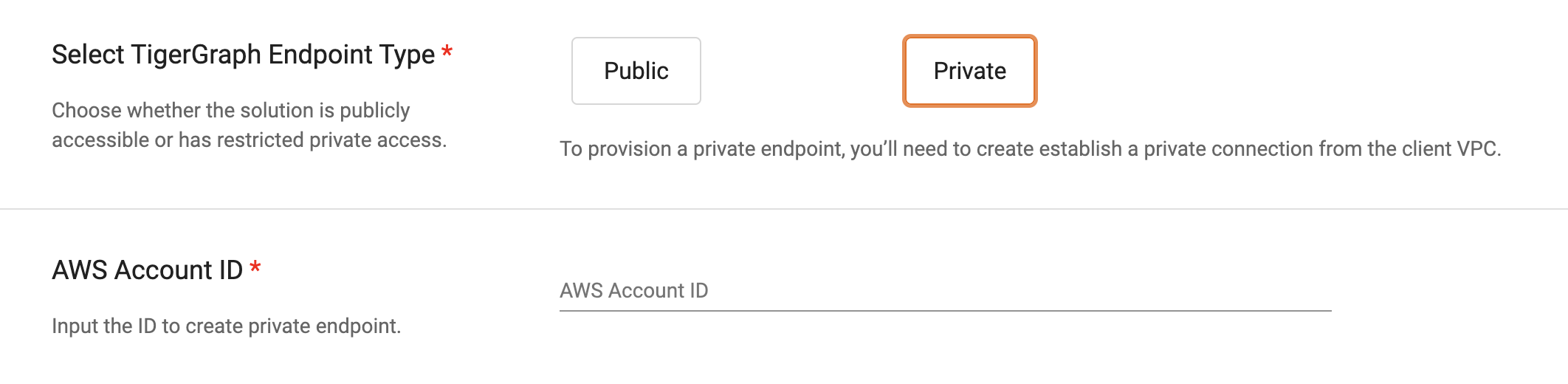
-
Fill in your AWS subscription ID. Behind the scenes, TigerGraph will provision an Endpoint Service and provide you with the Endpoint Service Name. The subscription ID that you provided will be added to the auto-approval allow list.
-
In your AWS account, create an endpoint using the Endpoint Service Name that TigerGraph provided.
-
Confirm on the TGCloud Portal that the endpoint has been created and TigerGraph will automatically approve it.
DNS Hostnames must be set to enabled in your VPC (Virtual Private Cloud) to use the TigerGraph private DNS.
See instructions at this link: View and update DNS attributes for your VPC
Instructions
Create VPC endpoint via console
AWS has detailed step-by-step instructions here: Access an AWS service using an interface VPC endpoint
-
Under Service Category, select Other endpoint services.
-
Check the box labeled Enable DNS name under Additional Settings if you are creating a VPC endpoint via the console.
|
The security group assigned to the VPC Endpoint created from the command must allow inbound and outbound connections on port 443. The security group assigned to the resource(s) used to communicate with the TigerGraph services through the Private Link MUST allow inbound and outbound connections on port 443. |
Create VPC endpoint via AWS CLI
Make sure you have the latest AWS CLI tools from this link: AWS Command Line Interface
The following IDs are necessary to generate the CLI command:
-
Customer VPC ID
-
Customer Subnet ID(s)
-
Customer AWS Account ARN, IAM Role ARN, or IAM User ARN (for automatic approval)
aws ec2 create-vpc-endpoint
--vpc-id vpc-ec43eb89
--vpc-endpoint-type Interface
--service-name com.amazonaws.vpce.us-east-1.vpce-svc-0a85faeb9b6f57977
--subnet-id subnet-1 subnet-2
--security-group-id sg-1a2b3
--region us-west-1If no security group is specified, the default security group for your VPC will be selected. In order to communicate with your TigerGraph cluster via AWS Private link, inbound and outbound connections to the TigerGraph services on port 443 must be allowed.